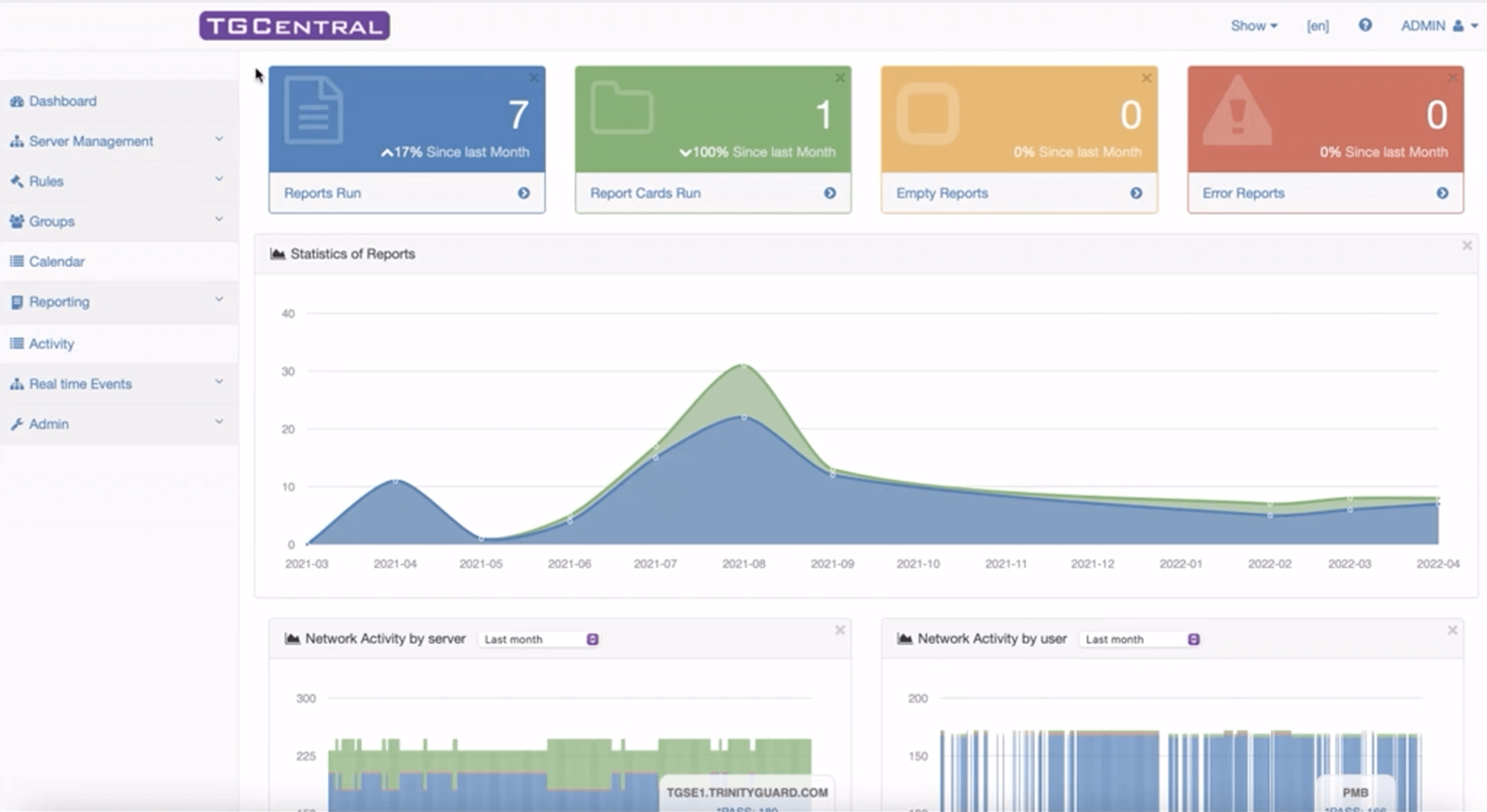
Business-critical data on IBM i is not immune to ransomware, cybercrimes, and data theft. Key areas of exposure include the files and directories in your IFS and network connectivity such as ODBC, FTP, web server applications, and other socket connections. Use the Fresche Security Suite to increase governance and compliance, mitigate risk, and deliver greater operational efficiency.
Ransomware Protection
Monitor traffic to your IBM i through exit-point connections like FTP telnet and ODBC, as well as socket layer access.
Exit Point Security
Lock down, monitor, get real-time notifications and access pre-defined security compliance reports, making it easy to meet ongoing compliance and regulatory requirements.
Compliance & Auditing
Protect sensitive and confidential data against unauthorized access and viewing by encrypting, masking, and scrambling fields and data.
Data Encryption
Encrypt, mask, and scramble field values so you can protect your data and comply with security regulations such as PCI and HIPAA. Track sensitive data access and get real-time alerts when sensitive data is accessed by users.
Intrusion Detection & SIEM Integration
Identify the right data to analyze and get alerts to security incidents as they occur is vital to stop intrusions and minimize internal and external threats.
Multi-Factor Authentication (MFA)
Implement an extra layer of security on user account access by requiring token entry in addition to passwords.